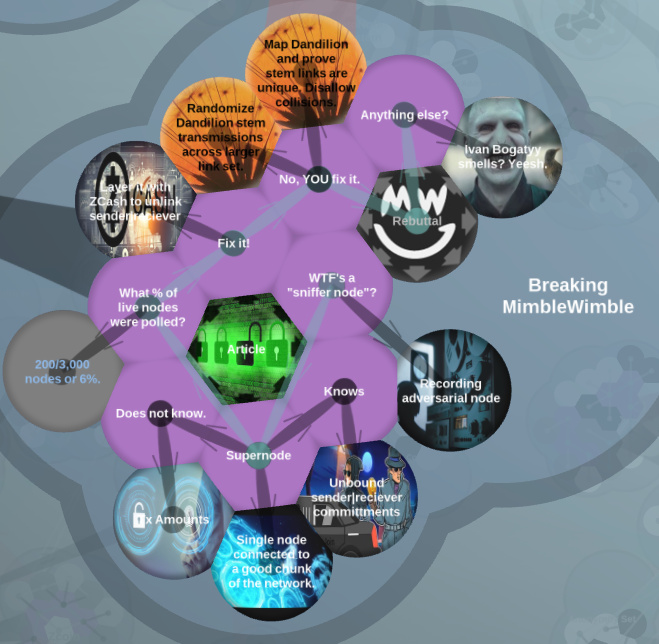
- Sniffer nodes pickup transactions through the whole network to disaggregate the blocks
- can determine who send who, not how much was sent
- 200 peers out of 3000 = 6.67%
- combine Mimblewimble with a Zerocash-style commitment-nullifier scheme to obscure the transaction graph. Decoy zerocoin outputs aggregated at the orginating broadcast.
- They pretty much debunked the claims that were made and would have to agree with the position that improvements on privacy are made compared to bitcoin’s privacy in a scalable manner on chain, yet without the need for trusted setup and high tx cost, and by default. The known limitations were no news for the development team, which the writer could have known, had he just asked. Seems like he preferred to write a clickbait article or spread FUD, though he kept some politeness as well.
Question:
The only thing that I do wonder, which is not entirely clear: although UTXOs aggregated in 1 block can be linked by deaggregation. However, if an observer would sniff multiple blocks, could he then even link UTXOs from different blocks. To my understanding, since MW uses One Time UTXOs, it would be impossible to link previous transactions from previous blocks to a UTXO from a certain block. Which basically means that only if the identity of both sides in 1 and the same transaction are unveiled, would it be useful information, however there is no way of retrieving a transaction graph of the history based on that information. Is this a correct understanding?

 )
)