Hi Joseph,
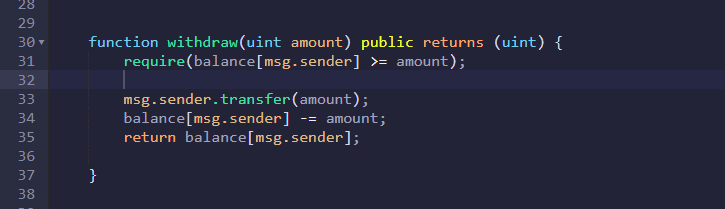
Your require statement and return statement are both now correctly positioned. All of the lines of code in your function body will now execute and perform all of the operations necessary to solve the initial problem with the withdraw function. 
More or less correct… We need to place require statements as near to the beginning of the function body as is practically possible because they validate INPUTS or restrict ACCESS.
assert() statements also handle errors, but as they are checking invariances (expected OUTPUTS), these are usually placed towards the end of the function body.
The other reason for placing require statements as near to the beginning of the function body as possible, is to keep the gas cost as low as possible in the event that require fails.
Solidity is a statically-typed programming language, but this doesn’t have anything to do with the top-to-bottom control flow that occurs during the execution of the code in a function body.
Your code will now compile and execute successfully, but to reduce security risk, it is important to modify the contract state for the reduction in the balance…
balance[msg.sender] -= amount;
before actually transferring the funds out of the contract to the external wallet address…
msg.sender.transfer(amount);
… just in case there is an attack after the transfer, but before the state is modified to reflect this operation. You’ll learn about the type of attack this prevents, and how it does it, in later courses. We wouldn’t expect you to know this at this early stage, though, so I’m just telling you for extra information. I think you must have misread my feedback to another student regarding this, but if you do think I’ve said the opposite somewhere, then please let me know, so I can check.
If the compiler icon is indicating an error (in red) or a warning (in orange) but is not highlighting the specific line in your code which is causing this, then you need to go to the Solidity Compiler panel by clicking on the icon with the number and scrolling down to the bottom of the panel where you will also find any error or warning messages (including any that you can’t access directly in the text editor). If you only have 1 orange warning, then I suspect it will be the ubiquitous:
Warning: SPDX license identifier not provided in source file.
Before publishing, consider adding a comment containing
"SPDX-License-Identifier: <SPDX-License>" to each file ...
This isn’t important because you aren’t publishing your code. However, I always include…
// SPDX-License-Identifier: UNLICENSED
… at the top of each of my files, just to get rid of this constant warning, because I find it annoying 
By the way, please don’t post screen shots of your code, because then we can’t copy it and run it ourselves, if necessary. We also can’t quote parts of it, which is also very useful when providing feedback. In this particular post of yours, it doesn’t really matter, but when other students see screen shots, they think it’s generally OK to post them too, and then it will just snowball. Thanks, for your understanding 
Let me know if you have any further questions about this assignment 




 but you are missing 2 other important lines of code, and there are couple of other mistakes which prevent your code from compiling:
but you are missing 2 other important lines of code, and there are couple of other mistakes which prevent your code from compiling:

